Data Security

Data privacy
Data stored about a person or an organisation must remain private and unauthorised access to the data must be prevented – data privacy is required.
This is achieved partly by data protection laws.
These laws vary from country to country, but all follow the same eight guiding principles.
- Data must be fairly and lawfully processed.
- Data can only be processed for the stated purpose.
- Data must be adequate, relevant and not excessive.
- Data must be accurate.
- Data must not be kept longer than necessary.
- Data must be processed in accordance with the data subject’s rights.
- Data must be kept secure.
- Data must not be transferred to another country unless that country also has adequate protection.
Data security
- Data security refers to the methods used to prevent unauthorised access to data, as well as to the data recovery methods if it is lost.
- User accounts are used to authenticate a user (prove that a user is who they say they are). User accounts are used on both standalone and networked computers in case the computer can be accessed by a number of people. This is often done by a screen prompt asking for a username and password, user accounts control access rights.
- Passwords are used to restrict access to data or systems. They should be hard to crack and changed frequently to retain security. Passwords can also take the form of biometrics.
Data privacy
Data stored about a person or an organisation must remain private and unauthorised access to the data must be prevented – is required
Data security
refers to the methods used to prevent unauthorised access to data, as well as to the data recovery methods if it is lost
Digital signatures
Digital signatures protect data by providing a way of identifying the sender of, for example, an email.
Digital signatures are a way of validating the authenticity of digital documents and identifying the sender.
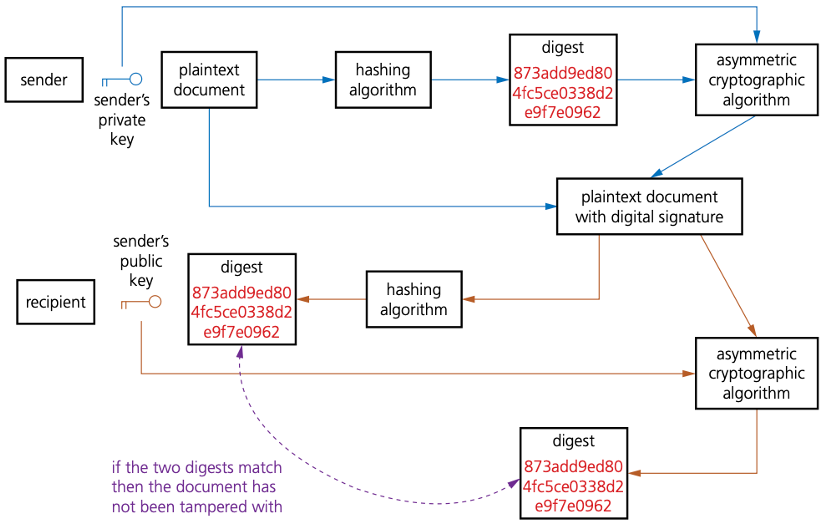
Data security
are a way of validating the authenticity of digital documents and identifying the sender.
Use of firewalls
- A firewall can be software or hardware. It sits between the user’s computer and an external network (such as the internet) and filters information in and out of the computer.
- The tasks carried out by a firewall include:
- examining the traffic between the user’s computer and a public network
- checking whether incoming or outgoing data meets a given set of criteria
- blocking the traffic if the data fails to meet the criteria, and giving the user a warning that there may be a security issue
- logging all incoming and outgoing traffic to allow later interrogation by the user
- preventing access to certain undesirable sites – the firewall can keep a list of all undesirable IP addresses
- helping to prevent viruses or hackers entering the user’s computer
- warning the user if some software on their system is trying to access an external data source. The user is given the option of allowing it to go ahead or request that such access is denied.
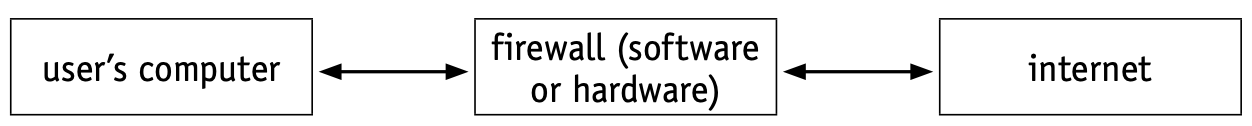
- The firewall can be a hardware interface which is located somewhere between the computer (or internal network external link) and the internet connection.
- In these cases, it is often referred to as a gateway. Alternatively, the firewall can be software installed on a computer, sometimes as part of the operating system.
- However, sometimes the firewall cannot prevent potential harmful traffic. It cannot:
- prevent individuals, on internal networks, using their own modems to by-pass the firewall
- control employee misconduct or carelessness
- prevent users on stand-alone computers from disabling the firewall.
Data security
The tasks carried out by a firewall include:
Antivirus software
- Running antivirus software in the background on a computer will constantly check for virus attacks.
- Although different types of antivirus software work in different ways, they all
- check software or files before they are run or loaded on a computer
- compare possible viruses against a database of known viruses
- carry out heuristic checking (check software for behaviour that could indicate a virus, which is useful if software is infected by a virus not yet on the database)
- quarantine files or programs which are possibly infected and
- allow the virus to be automatically deleted, or
- allow the user to make the decision about deletion (it is possible that the user knows that the file or program is not infected by a virus – this is known as a false positive and is one of the drawbacks of antivirus software).
Data security
Running in the background on a computer will constantly check for virus attacks
Anti-spyware software
- Anti-spyware software detects and removes spyware programs installed illegally on a user’s computer system.
- The software is either based on rules (it looks for typical features associated with spyware) or based on known file structures which can identify common spyware programs.
Data security
software detects and removes spyware programs installed illegally on a user’s computer system.
Encryption
If data on a computer has been accessed illegally (by a hacker, for example) it is possible to encrypt the data, making it virtually impossible to understand without encryption keys to decode it.
This cannot stop a hacker from deleting the files, but it will stop them using the data for themselves.
The original data being sent is known as plaintext. Once it has gone through an encryption algorithm, it produces ciphertext.
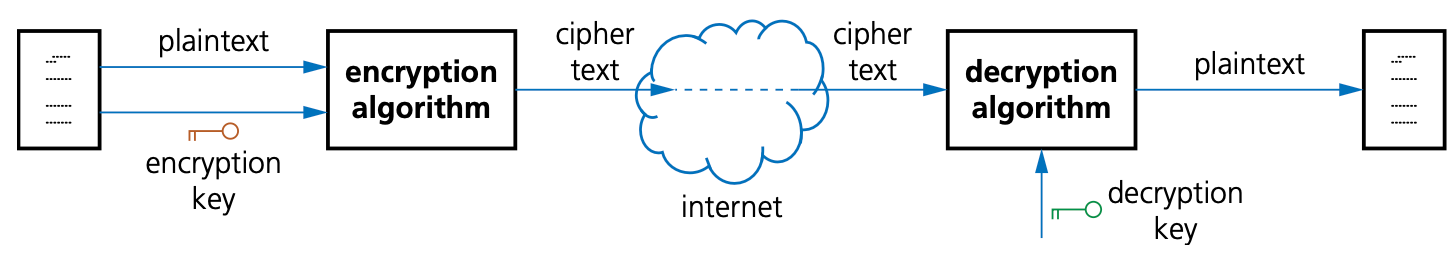
Data security
The original data being sent is known as plaintext. Once it has gone through an algorithm, it produces ciphertext.
Biometrics
- In an attempt to stay one step ahead of hackers and malware writers, many modern computer devices use biometrics as part of the password system.
- Biometrics rely on the unique characteristics of human beings.
- Examples include fingerprint scans, retina scans (pattern of blood capillary structure), face recognition and voice recognition.

Data security
rely on the unique characteristics of human beings.
Hacking
- There are two types of hacking: malicious and ethical.
- Malicious hacking is the illegal access to a computer system without the user’s permission or knowledge. It is usually employed with the intention of deleting, altering or corrupting files, or to gain personal details such as bank account details. Strong passwords, firewalls and software which can detect illegal activity all guard against hacking.
- Ethical hacking is authorised by companies to check their security measures and how robust their computer systems are to resist hacking attacks. It is legal, and is done with a company’s permission with a fee paid to the ethical hacker.
Data security
Malicious is the illegal access to a computer system without the user’s permission or knowledge.
Malware
- Malware is one of the biggest risks to the integrity and security of data on a computer system.
- Many software applications sold as antivirus are capable of identifying and removing most of the forms of malware described below.
- Viruses are programs or program code that can replicate and/or copy themselves with the intention of deleting or corrupting files or causing the computer to malfunction.
- Worms are a type of stand-alone virus that can replicate themselves with the intention of spreading to other computers; they often use networks to search out computers with weak security.
- Logic bombs are code embedded in a program on a computer. When certain conditions are met (such as a specific date) they are activated to carry out tasks such as deleting files or sending data to a hacker.
- Trojan horses are malicious programs often disguised as legitimate software. They replace all or part of the legitimate software with the intent of carrying out some harm to the user’s computer system.
- Bots (internet robots) are not always harmful and can be used, for example, to search automatically for an item on the internet. However, they can cause harm by taking control over a computer system and launching attacks.
- Spyware is the software that gathers information by monitoring, for example, key presses on the user’s keyboard. The information is then sent back to the person who sent the software – sometimes referred to as key logging software.
Data security
is one of the biggest risks to the integrity and security of data on a computer system.
Phishing
Phishing is when someone sends legitimate-looking emails to users.
They may contain links or attachments which, when clicked, take the user to a fake website, or they may trick the user into responding with personal data such as bank account details or credit card numbers.
The email often appears to come from a trusted source such as a bank or service provider.
The key is that the recipient has to carry out a task (click a link, for example) before the phishing scam causes harm.
There are numerous ways to help prevent phishing attacks:
- Users need to be aware of new phishing scams.
- Do not click on links unless certain that it is safe to do so
- It is important to run anti-phishing toolbars on web browsers since these will alert the user to malicious websites contained in an email.
- Look out for https and/or the green padlock symbol in the address bar
- Regularly check online accounts and frequently change passwords.
- Ensure an up-to-date browser, with all of the latest security upgrades, is running, and run a good firewall in the background at all times.
Data security
is when someone sends legitimate-looking emails to users.
Pharming
Pharming is malicious code installed on a user’s computer or on a web server.
The code re-directs the user to a fake website without their knowledge (the user does not have to take any action, unlike phishing).
The creator of the malicious code can gain personal data such as bank details from users.
Often, the website appears to belong to a trusted company and can lead to fraud or identity theft.
Pharming redirects users to a fake or malicious website set up by, for example, a hacker.
Redirection from a legitimate website can be done using DNS cache poisoning.
It is possible to mitigate the risk of pharming by
- using antivirus software, which can detect unauthorised alterations to a website address and warn the user
- using modern web browsers that alert users to pharming and phishing attacks
- checking the spelling of websites
- checking for https and/or the green padlock symbol in the address bar
Data security
is malicious code installed on a user’s computer or on a web server.
Data recovery
- This section covers the potential impact on data caused by accidental mal-operation, hardware malfunction and software malfunction.
- In all cases, the backing up of data regularly onto another medium is key to data recovery.
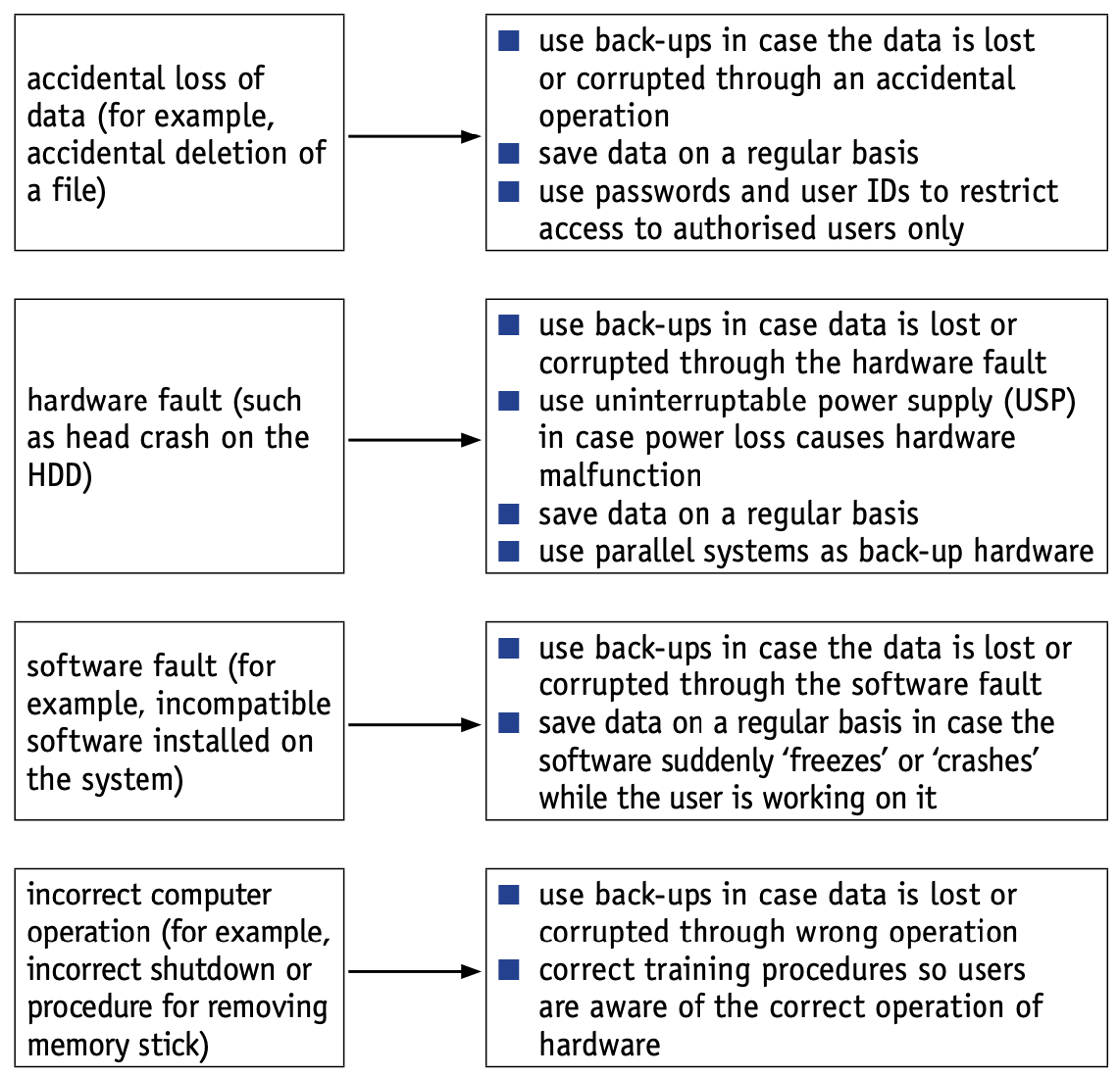
Data security
The potential impact on data could be caused by: